Identifying WannaCry on Your Server Using Logs
WannaCry (also known as WannaCrypt or WCry) is the latest ransomware attack to rapidly spread across the Internet. What makes this attack different from others is its success at both encrypting data and self-replication. A major factor is that the malware is based on leaked NSA code named EternalBlue, which was created to exploit Windows SMBv1. WannaCry spread like wildfire, hitting over 70 countries and crippling major businesses including FedEx, NHS, Spain’s major telephony provider Telefonica, and Gas Natural.
Global #WannaCry Infection Map | #cybersecurity #infosec #Ransomware #security #malware #cyberattacks #cybercrime #hacking #hackers #exploit pic.twitter.com/u3BtI9NnHW
— TheCyberSecurityHub (@TheCyberSecHub) May 15, 2017
The ransomware works similarly to lesser-known ransomware in the wild. Once WannaCry spreads to a system, it searches for specific file extensions, mainly ones that the authors know are important to the victim. Anything from images to documents to presentations are then encrypted with a 2048-bit RSA key. The only way to decrypt these files is with the private key, which costs victims $300. If you wait too long, you must pay double the price at $600. Researchers estimate that the authors have already made $70,000.
How the Malware Spreads
Usually, ransomware authors spread their malware using malicious file attachments in email. They either attach the malware directly to the email, or they use macros in Microsoft documents that install Trojans that then download the ransomware. WannaCry works differently, which is why has been so effective at infecting machines and generating headlines. No user interaction is necessary for WannaCry to spread.
WannaCry takes advantage of an old Windows SMB bug. SMBv1, used for file sharing among Linux and other Windows hosts, is an outdated protocol and should be disabled on your network. It has long been outdated, but some Windows administrators keep it active for legacy applications or just for convenience.
When WannaCry sees an open file share, it creates a copy across the network. Since so many administrators leave SMBv1 active, the malware was able to spread quickly especially in a Windows network environment.
Another interesting component of WannaCry was its “kill switch” behavior. The ransomware queries a unique domain name that seemingly has no meaning other than being a long string of random characters. Researchers believe that this domain was coded into the malware to stop it from working, probably in case authors felt that they were caught or needed it to stop for personal reasons. By registering the domain name “iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com”, researchers were able to stop the effects of WannaCry. Several variants have been made, so this list of domain names as kill switches has increased.
How to Use Logs to Detect and Stop WannaCry
Your first course of action should be to disable SMBv1 on your Windows machines if it’s an option. Since the malware uses SMB, even machines behind a firewall aren’t protected, so it’s imperative that you monitor for suspicious traffic to catch and stop WannaCry.
If you’re lucky enough to avoid file encryption with a working server intact, you can still detect WannaCry on your network should the executable file stay active on file shares. You might have copies of the ransomware hosted on file shares and not even know it. As with any malware, you must be proactive to prevent the software from spreading to other hosts before your entire network is lost to ransomware.
A few key events happen when your network has WannaCry installed on it:
- File creation specifically for encrypting files with WannaCry’s own document extension
- Outbound traffic for SMBv1’s ports TCP 445 and 139
- DNS queries for the domain iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
- Creates Windows registry entries
All four of these events can be tracked and monitored. Monitoring is the key to detecting WannaCry as well as other types of malware that spread across the network. Loggly can complement network monitoring and other tools you use on a regular basis.
WannaCry encrypts several types of documents and then appends the extension “.WNCRY” to them. If you have any folder auditing on your Windows directories, you can detect this event.
You can also check the Windows registry for the following two entries:
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\\<random string> = “<malware working directory>\tasksche.exe”
- HKLM\SOFTWARE\WanaCrypt0r\\wd = “<malware working directory>”
Both file creation and registry key entries can be checked manually on the local server, or you can run a PowerShell script to check for these events. The other two events can be checked using monitoring solutions such as Loggly.
If you send your system files to Loggly, you can use it to check for outbound TCP requests on ports 139 and 445. These two ports are specific to SMB, and an increase in queries on them should raise suspicions.
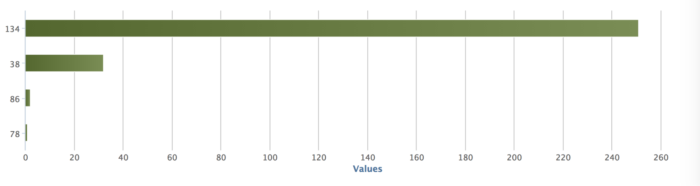
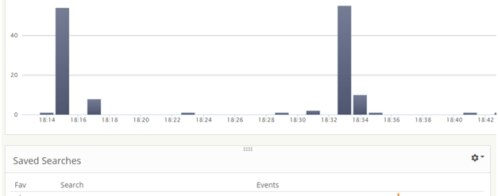
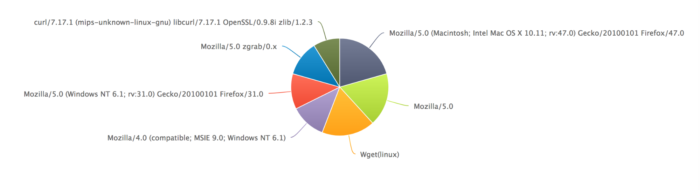
The second way Loggly can help you detect WannaCry is by monitoring and reviewing DNS queries. You can review DNS queries for the domain iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, which undoubtedly means your network is infected. Users reading news about WannaCry could also try to browse this domain, so you’ll need to differentiate standard browser queries from automated requests. This could be done by checking data such as the browser’s unique USER_AGENT value.
How Do You Stop WannaCry from Affecting Your Network?
If you get through this attack unscathed, it’s time to patch your Windows systems. The attack was so effective that Microsoft even released patches for Windows 2003, XP and Windows 8, which have long been deprecated. The only operating system unaffected by WannaCry is Windows 10, but you should still keep this operating system up-to-date.
All Windows machines should be updated with the latest update. If you have your Windows servers set to automatically update the operating system, then your servers should have defenses against the malware. Use Windows Update to download the latest patch including the new Windows Defender signatures used to detect WannaCry.
Several new variants for WannaCry have already been reported, so continue to monitor your network to protect from new versions released in the wild. These variants use new domain names as kill switches, but you can still monitor events on ports 445 and 139 to effectively stay alert to suspicious traffic. Monitoring these events will alert you to suspicious behavior from any malware that takes advantage of SMBv1 including the original WannaCry and its variants.
One way Loggly makes monitoring easier for you is that you can bring all of your data—from both servers and routers—in one location. You don’t need to check individual routers and servers for infection. Just hop onto your Loggly account, create a query, review results for any number of network resources to find out if you could be a victim, and then set alerts to prevent future surprises!
The Loggly and SolarWinds trademarks, service marks, and logos are the exclusive property of SolarWinds Worldwide, LLC or its affiliates. All other trademarks are the property of their respective owners.
Jennifer Marsh